From Fedora Project Wiki
(Created page with "{{QA/Test_Case |description=This test case tests {{package|usbguard}} GUI application. |setup= # This is a GUI application test, therefore you have to execute this test in a g...") |
No edit summary |
||
| (2 intermediate revisions by the same user not shown) | |||
| Line 8: | Line 8: | ||
# Prepare a USB device which is not connected to the system and for which there's no rule in your USBGuard policy. | # Prepare a USB device which is not connected to the system and for which there's no rule in your USBGuard policy. | ||
# Make sure that the user under whom you'll be testing the GUI application is a member of the wheel group. Otherwise the application won't have permissions to talk to the usbguard-daemon component. | # Make sure that the user under whom you'll be testing the GUI application is a member of the wheel group. Otherwise the application won't have permissions to talk to the usbguard-daemon component. | ||
{{admon/tip|How to get to a clean state|As root, run | {{admon/tip|How to get to a clean state|As root, run {{command|systemctl stop usbguard}} and {{command|killall usbguard-applet-qt}} and restore your policy from a backup.}} | ||
{{admon/tip|Where is my policy stored?|The USBGuard policy is stored in the file /etc/usbguard/rules.conf. Just copy the file somewhere else to make a backup. Copy it back and restart the usbguard service to restore the policy from the backup.}} | {{admon/tip|Where is my policy stored?|The USBGuard policy is stored in the file '''/etc/usbguard/rules.conf'''. Just copy the file somewhere else to make a backup. Copy it back and restart the usbguard service to restore the policy from the backup.}} | ||
|actions= | |actions= | ||
<ol type="l"> | |||
<li>Start the usbguard service: <pre># systemctl start usbguard</pre></li> | |||
<li>Start the usbguard-applet-qt application.</li> | |||
<li>Insert the USB device.</li> | |||
</li>Click on the '''block''' button to block the device. Check that the device remained blocked and is '''not''' usable.<br> | |||
[[File:usbguard-applet-qt-dialog-block.png|usbguard-applet-qt dialog]] | |||
</li> | |||
<li>Re-insert the USB device.</li> | |||
<li>Click on the '''allow''' button to allow the device. Check that the device is working as expected, e.g. if it's a USB mouse, then you can move the cursor with it.<br> | |||
[[File:usbguard-applet-qt-dialog-allow.png|usbguard-applet-qt dialog]] | |||
</li> | |||
<li>Re-insert the USB device.</li> | |||
<li>Check the "'''[ ] Make the decision permanent'''" option and click on the '''allow''' button.<br> | |||
[[File:usbguard-applet-qt-dialog-permanent.png|usbguard-applet-qt dialog]] | |||
</li> | |||
<li>Re-insert the USB device.</li> | |||
<li>The device should be automatically allowed. Check whether it's working as expected.</li> | |||
</ol> | |||
|results= | |results= | ||
# The application connects to the usbguard-daemon component on start. | # The application connects to the usbguard-daemon component on start. | ||
Latest revision as of 11:30, 22 August 2016
Description
This test case tests ![]() usbguard
usbguard
Setup
- This is a GUI application test, therefore you have to execute this test in a graphical session.
- Ensure the
 usbguard
usbguard usbguard-applet-qt
usbguard-applet-qt - Backup your policy because the testing procedure will modify it.
- To start from a clean state, ensure that the usbguard service is stopped and that the usbguard-applet-qt application is not running either.
- Prepare a USB device which is not connected to the system and for which there's no rule in your USBGuard policy.
- Make sure that the user under whom you'll be testing the GUI application is a member of the wheel group. Otherwise the application won't have permissions to talk to the usbguard-daemon component.
How to test
- Start the usbguard service:
# systemctl start usbguard
- Start the usbguard-applet-qt application.
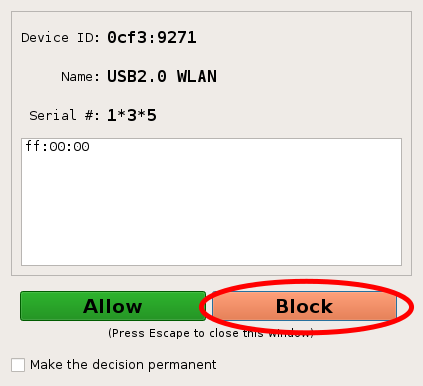
- Insert the USB device. Click on the block button to block the device. Check that the device remained blocked and is not usable.
- Re-insert the USB device.
- Click on the allow button to allow the device. Check that the device is working as expected, e.g. if it's a USB mouse, then you can move the cursor with it.
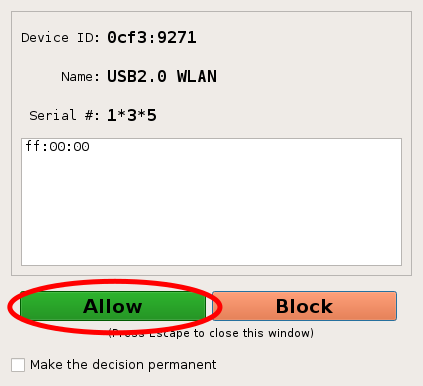
- Re-insert the USB device.
- Check the "[ ] Make the decision permanent" option and click on the allow button.
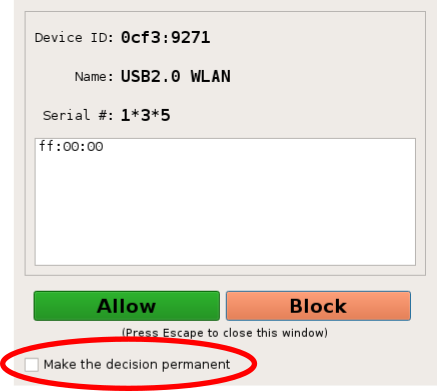
- Re-insert the USB device.
- The device should be automatically allowed. Check whether it's working as expected.
Expected Results
- The application connects to the usbguard-daemon component on start.
- A device dialog appears when the USB device is connected to the system.
- The allow and block buttons work as expected.
- If the "[ ] Make the decision permanent" option is checked, then the action is remembered and no device dialog appears for the device again.
